Password compromises continue to be a leading security issue for organizations and their customers. 46% of Forbes’ U.S. OnePoll survey respondents say their passwords were breached in the past year.
There are many reasons why passwords can become compromised. Sometimes, it’s something as simple as hardcoding your credentials into applications. But in most cases, these situations occur as the result of various password cracking methods.
This is why today’s lesson will examine 9 password cracking attacks. We want you to understand these credential-compromising methods and what you can do to stop them.
Let’s hash it out.
A 30-Second Review: What Is a Password Cracking Attack?
Let’s start by quickly covering the basics (i.e., what a password cracking attack is) before moving on to the specific techniques. In a nutshell, password cracking is a way for someone to gain unauthorized access to a password.
Of course, many methods and techniques can be used to achieve this goal. But when drilling right down to the heart of the issue, password-cracking attacks target either the technical or non-technical vulnerabilities (or both) that exist within your organization’s IT ecosystem.
What Are the 4 Categories of Password Cracking?
Of course, industry professionals have different ideas about what constitutes password cracking. But we’ll run with Michael Solomon’s and Sean-Philip Oriyano’s definition for the sake of this article.
In their book “Ethical Hacking: Techniques, Tools, and Countermeasures (4th Edition)” Solomon and Oriyano identify four overarching categories of password cracking methods:
- Active online attacks — These attacks involve threat actors taking deliberate actions, such as by using massive lists of guessed username-password combinations to force their way into legitimate accounts.
- Passive online attacks — Examples of these types of attacks include man-in-the-middle (MitM) attacks and packet sniffing. Basically, this more laid-back approach takes advantage of someone’s insecure connections and vulnerable technologies.
- Offline attacks — These attacks don’t require intercepting data in transit or poor choices of passwords. They instead focus on the security mechanisms relating to how and in what formats the passwords are stored.
- Non-technical attacks — These methods involve exploiting your employees’ and other users’ lack of cyber awareness and bad password security practices (e.g., their choice to use weak or recycled passwords).
Basically, these attacks focus on the security mechanisms you use to protect passwords and the humans you have working within your network and other IT environments. They exploit vulnerabilities that exist within your authentication systems, server configurations, and employees’ security practices.
9 Common Password Cracking Methods That Can Harm Your Business
Alright, it’s time to start exploring some of the most popular password cracking techniques and mechanisms bad guys love to use. For this article, we’ve divided these password cracking methods based on what the attacker does and what (or whom) they target.
Taking Advantage of Employees’ Human Nature
I hate to break the news… but like you and me, your employees are human. Humans make mistakes. Sometimes, these mistakes include using weak passwords that are easy to guess. In other situations, they may be tricked or manipulated into sharing their secrets.
No one is infallible. For example, you or a colleague might accidentally misconfigure your password database, leaving the secrets within vulnerable. Although a security misconfiguration isn’t an example of password cracking specifically, it just shows that even IT professionals aren’t infallible. And if the pros make mistakes, then it can be expected that less tech- and security-savvy employees will as well.
But rather than pointing fingers, our point here is that these types of human error-based mistakes result in handing bad guys your now-compromised credentials on a silver platter. Regardless of how a password compromise occurs, the bottom line is that these issues frequently stem from human-related vulnerabilities, and all it takes is one “oops” for your day to go from good to bad.
Verizon’s 2023 DBIR data indicates that 74% of data breaches involved the human element. Knowing this, it’s time to explore four of the ways that bad guys love to exploit human-based vulnerabilities.
1. Phishing Attacks and Social Engineering
First on our list of password cracking methods is phishing. A phishing attack typically involves bad guys sending fraudulent emails, setting up fake websites, or even making phony phone and video calls to achieve their goals. Even generative AI tools can play a role in carrying out these scams!
In some cases, cybercriminals will go the extra mile by pairing these outreach methods with social engineering tactics. The goal? To exploit human emotions, fears, and responses to seemingly urgent situations. They’ll often create fake emergencies or urgent situations to trick or manipulate an employee into doing their bidding (e.g., sharing their passwords).
Here’s an example of a phishing scam in which an attacker impersonates Microsoft and pretends that my colleague has been charged for software he didn’t buy:
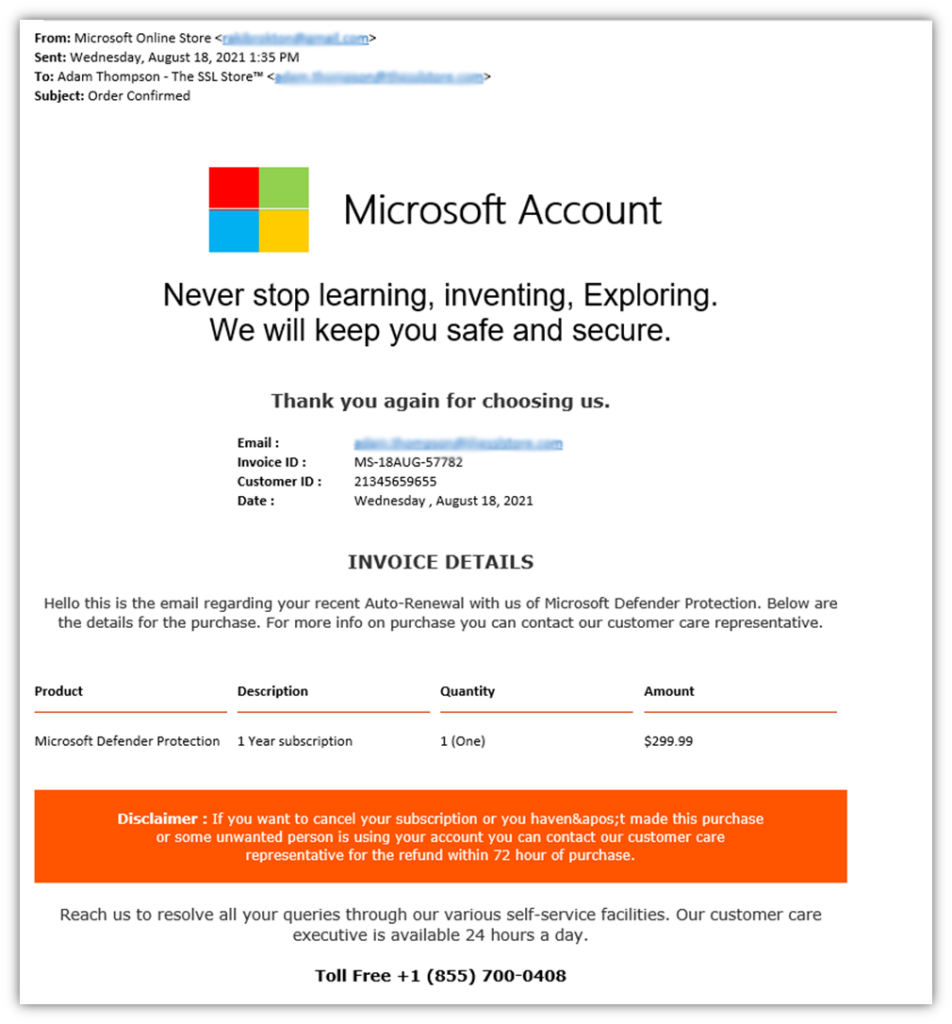
Furthermore, researching their target helps the attacker make more informed guesses about possible passwords that the person may use. For example, passwords that include the names or birthdates of children, pets’ names, and important dates such as anniversaries will be easier for a bad guy to guess.
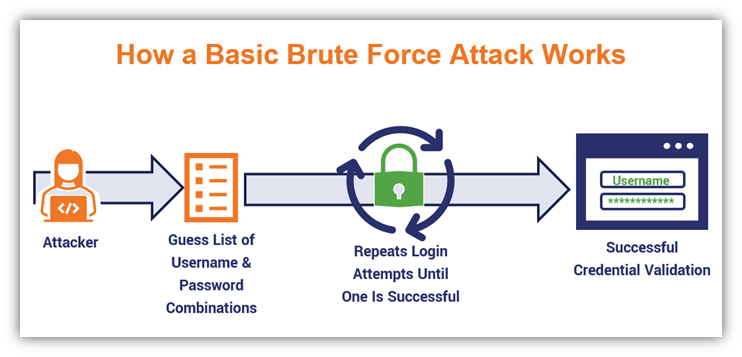
2. Brute Force Attacks
The name alone pretty much tells you what you need to know. A brute force attack is a password cracking method that involves a bad guy trying to force their way into legitimate accounts by guessing combinations of usernames and passwords until they find a successful match.
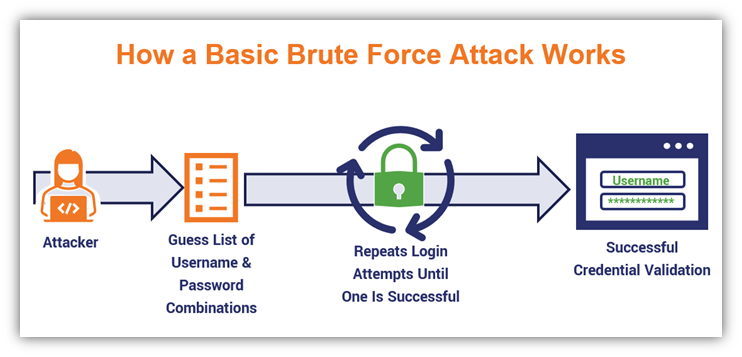
It’s important to note here that “brute force” is both a category of password attack as well as a specific attack method. (Not too confusing, right?) Although this and the following two items on the list technically fall within the category of brute force attacks, I’m separating them as individual types of password cracking attacks because bad guys go about carrying them out in different ways.
If an attacker takes the time to research the company and discover any password-related rules, it helps to narrow down the number of choices they’d have to guess. For example, if you know a company requires a password between 8 and 12 characters, and only certain special characters are allowed, then that narrows down the pool significantly.
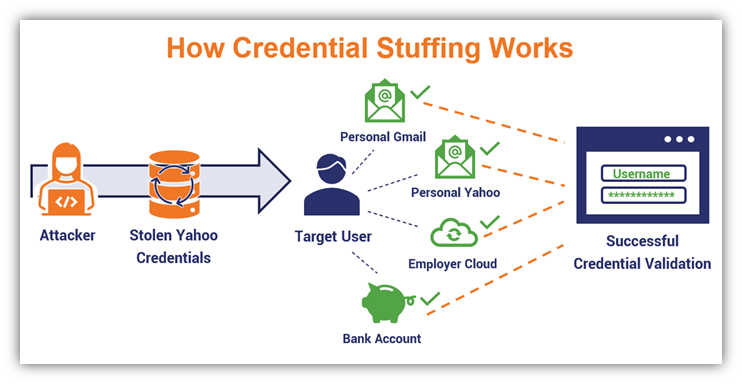
3. Credential Stuffing Attacks
Similar to brute force attacks, credential stuffing attacks also involve an attacker using a long list of username and password combinations. However, in this case, the attacker has a list of previously compromised credentials they use botnets to try out on various web apps until they get a hit.
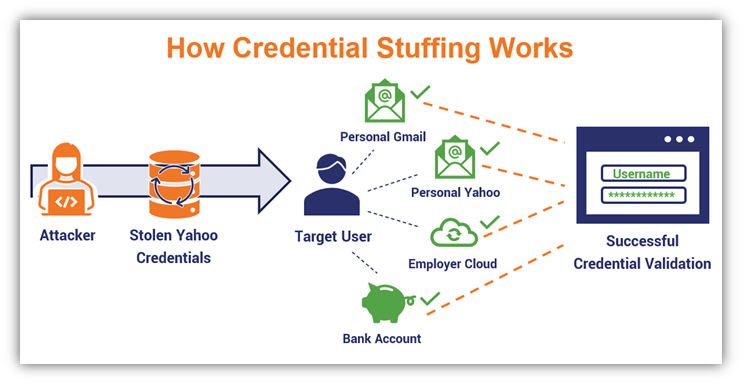
This approach typically involves using lists of usernames and passwords that have been leaked or stolen in previous data breaches. Cybercriminals frequently sell, barter, and share compromised credentials on the dark web. They also use information about the target to help calculate and guess additional passwords.
This underscores the importance of ensuring that employees get into the habit of changing their usernames and passwords whenever there’s a breach. Be sure to remind them to use new, unique passwords and not reuse old ones from other accounts…
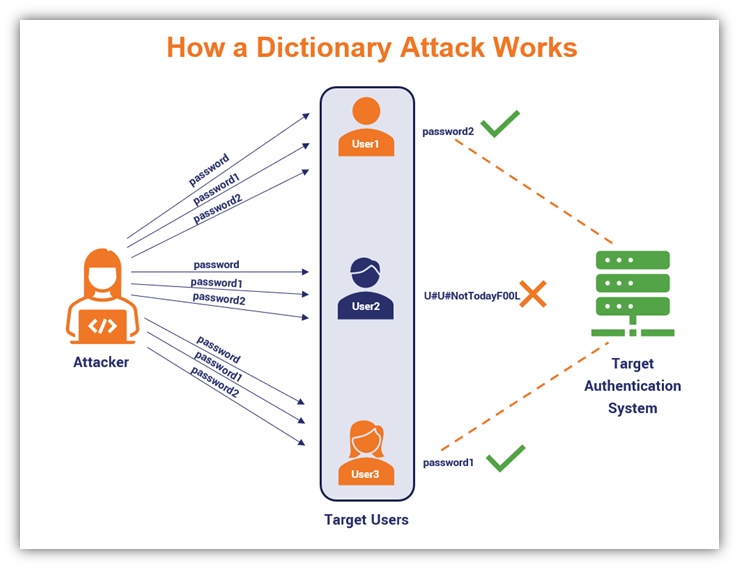
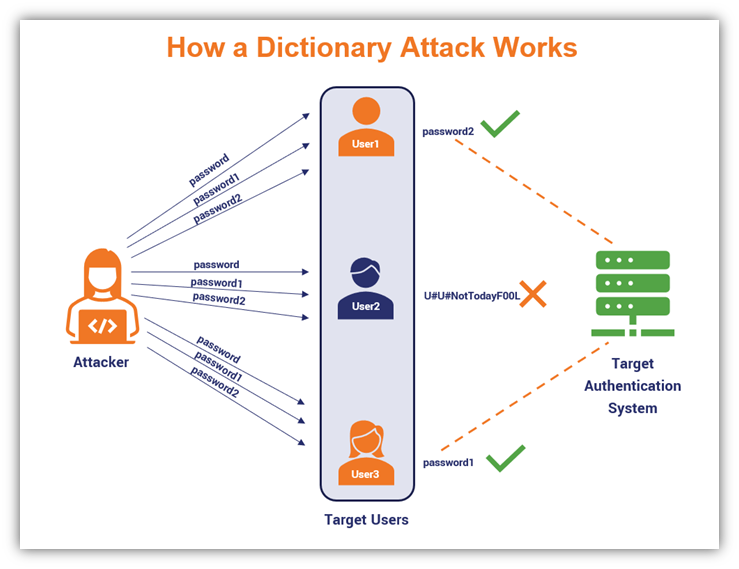
4. Dictionary Attacks
This type of password-focused attack involves using a massive, predefined list of common words that you can find in a dictionary. An attacker then builds upon this list to create as many permutations as possible, often using password cracking tools that help simplify or speed up the task.
Using Password Cracking Tools and Services
It’s no secret that threat actors often love malicious scripts and malware. For example, some use keyloggers to get their grubby hands on users’ credentials. But those aren’t the only types of tools that are useful for achieving the end result of snagging passwords…
5. Password-Cracking Software
Password cracking software is an application that’s used to crack passwords. Some are application- or file-specific, and virtually none are the instant fixes that movies and TV shows make them out to be. These tools aren’t instantaneous and require preparations to be made in terms of creating the password lists that an attacker will use.
Examples of popular password cracking tools and services include Aircrack-ng, RainbowCrack, John the Ripper, and Ophcrack.
Now, we’re not here to provide a tutorial for bad guys. However, these tools do serve legitimate uses for organizations’ cyber security teams (we’ll speak more about that later).
6. Packet Sniffing Tools
Packet sniffing solutions are useful tools for cybersecurity experts. They enable attackers to eavesdrop on communications, much like a man-in-the-middle (MitM) situation, but it’s more passive than active.
When used by ethical hackers and IT teams, they can be useful in helping to identify vulnerable traffic. But when used in the wrong hands, these tools can be used to do the same tasks (e.g., network and traffic monitoring) for different purposes and much uglier outcomes.
A packet sniffer can be used to detect and capture passwords as they move between two devices on a network. Examples of popular packet sniffing tools include the opensource packet analyzer tools Wireshark and tcpdump.
Just keep in mind, however, that packet-sniffing tools can sniff data on HTTPS connections. But if the attacker doesn’t have access to the private key that’s required to decrypt the secure data, all the attacker will see is a bunch of gibberish.